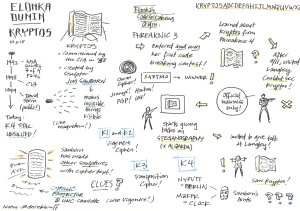
Not only is Elonka Dunin able to solve extremely difficult codes and ciphers, but she is also able to create them and teach others the techniques to solve them, which truly shows a mastery of the skill. She illustrates this talent in her book that was released in 2006 called The Mammoth Book of Secret Codes and Cryptograms. I really want to read this book because it includes a wide range of fun brain teasers such as secret messages, substitution ciphers, historical ciphers used by Julius Caesar or JFK, etc. She also includes tips to solve some of the most famous ciphers in history such as the fourth section of Kryptos or the Zodiac Killer ciphers.
The book seems like a fun and interactive way to extend my knowledge and cryptography, and it also relates to some of the things we have discussed in class this year. Of course, it include Kryptos which Elonka Dunin came in to teach us a little about, but we have also learned about the Caesar ciphers (substitution ciphers where the alphabet is just shifted), and we probably have the tools to solve some of the low to medium levels of ciphers that she includes in her text. Overall, I am excited to read her book because it will be an interactive way to learn how to solve more difficult ciphers and extend my knowledge on the history of cryptography.